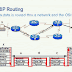
Routing Information Protocol (RIP) By :- Network-Facts
 Roting Information Protocol (RIP) is a standards-based, distance-vector, interior gateway protocol (IGP) used by routers to exchange routing information. RIP uses hop count to determine the best path between two locations. Hop count is the number of routers the packet must go through till it reaches the destination network. The maximum allowable number of hops a packet can traverse in an IP network implementing RIP is 15 hops.
Roting Information Protocol (RIP) is a standards-based, distance-vector, interior gateway protocol (IGP) used by routers to exchange routing information. RIP uses hop count to determine the best path between two locations. Hop count is the number of routers the packet must go through till it reaches the destination network. The maximum allowable number of hops a packet can traverse in an IP network implementing RIP is 15 hops.
it has a maximum allowable hop count of 15 by default, meaning that 16 is deemed unreachable. RIP works well in small networks, but it's inefficient on large networks with slow WAN links or on networks with a large number of routers installed.
In a RIP network, each router broadcasts its entire RIP table to its neighboring routers every 30 seconds. When a router receives a neighbor's RIP table, it uses the information provided to update its own routing table and then sends the updated table to its neighbors.
Differences between RIPv1 or RIPv2
RIPv1
· A classful protocol, broadcasts updates every 30 seconds, hold-down period 180 seconds. Hop count is metric (Maximum 15).
· RIP supports up to six equal-cost paths to a single destination, where all six paths can be placed in the routing table and the router can load-balance across them. The default is actually four paths, but this can be increased up to a maximum of six. Remember that an equal-cost path is where the hop count value is the same. RIP will not load-balance across unequal-cost paths
RIPv2
· RIPv2 uses multicasts, version 1 use broadcasts,
· RIPv2 supports triggered updates—when a change occurs, a RIPv2 router will immediately propagate its routing information to its connected neighbors.
· RIPv2 is a classless protocol. RIPv2 supports variable-length subnet masking (VLSM)
· RIPv2 supports authentication. You can restrict what routers you want to participate in RIPv2. This is
accomplished using a hashed password value.
· RIP uses four different kinds of timers to regulate its performance:
· Route update timer
· Sets the interval (typically 30 seconds) between periodic routing updates in which the router sends a complete copy of its routing table out to all neighbors.
· Route invalid timer
· Determines the length of time that must elapse (180 seconds) before a router determines that a route has become invalid. It will come to this conclusion if it hasn’t heard any updates about a particular route for that period. When that happens, the router will send out updates to all its neighbors letting them know that the route is invalid.
· Holddown timer
· This sets the amount of time during which routing information is suppressed. Routes will enter into the holddown state when an update packet is received that indicated the route is unreachable. This continues either until an update packet is received with a better metric or until the holddown timer expires. The default is 180 seconds.
· Route flush timer
· Sets the time between a route becoming invalid and its removal from the routing table (240 seconds). Before it's removed from the table, the router notifies its neighbors of that route's impending failure. The value of the route invalid timer must be less than that of the route flush timer. This gives the router enough time to tell its neighbors about the invalid route before the local routing table is updated.